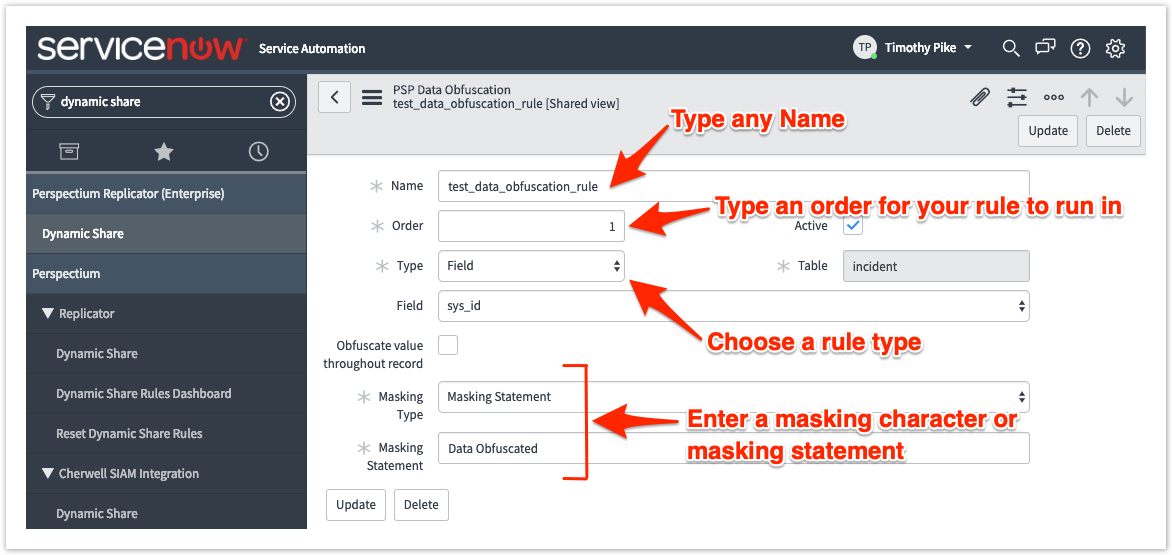
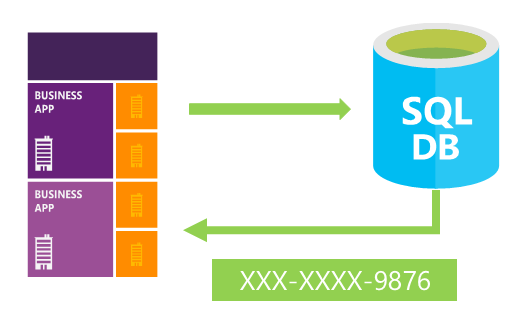
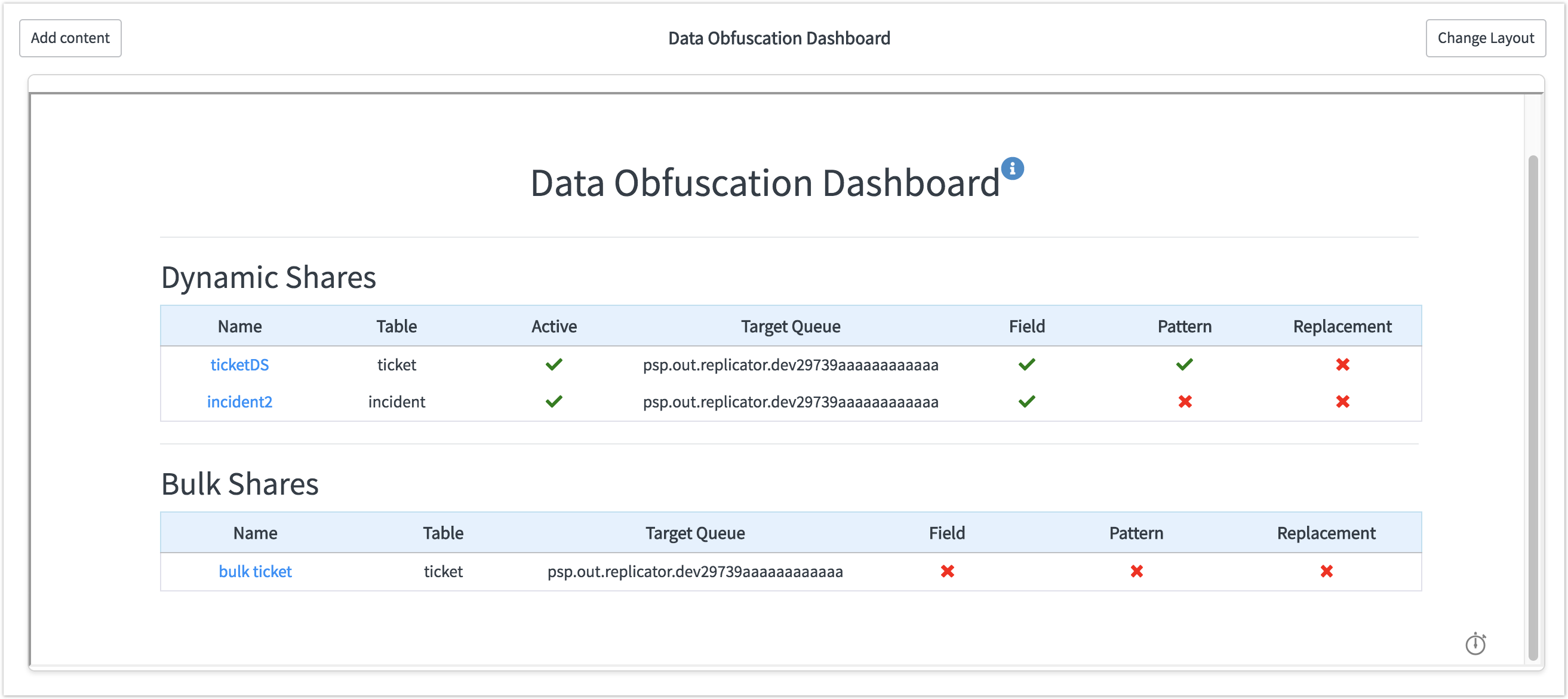
MySQL Security – MySQL Enterprise Data Masking and De-Identification | dasini.net - Diary of a MySQL experts
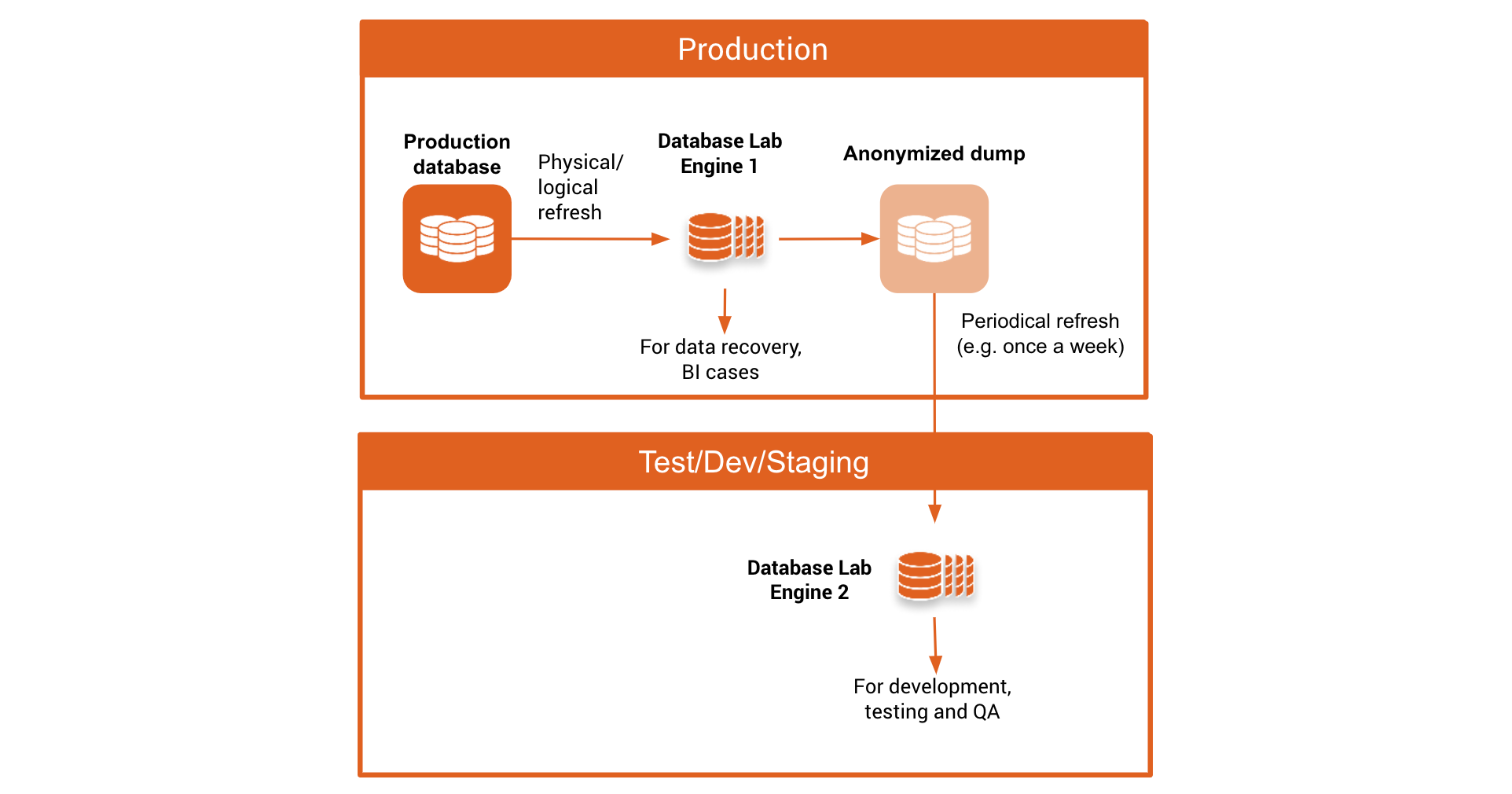
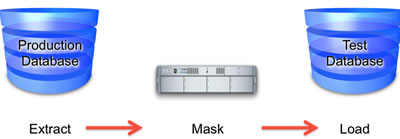
Database Lab data masking and obfuscation | Database Lab · Instant clones of PostgreSQL databases · Postgres.ai
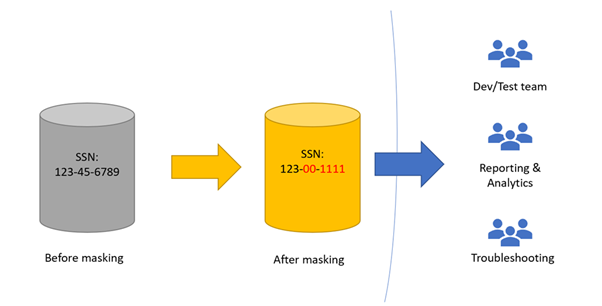
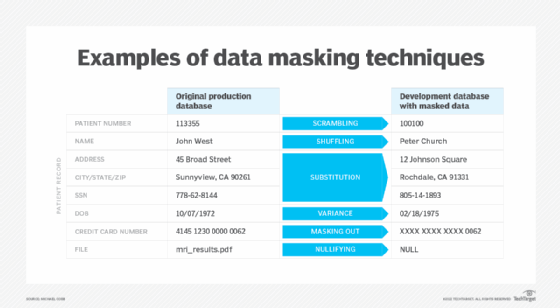
Data Masking : Concept, Tools, Masking polices & Healthcare Data Masking | by Samadhan Kadam | Petabytz | Medium

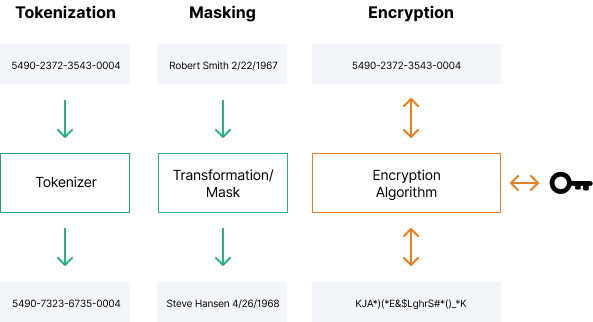
Taking charge of your data: using Cloud DLP to de-identify and obfuscate sensitive information | Google Cloud Blog